Manage Security Roles
The Manage Security Roles plugin in the Administrative Console (Security Admin > Setup) is used to create and maintain the security roles in BusinessPlus. Manage Security Roles was previously accessible via BusinessPlus mask NUUPSR.
Security Objects
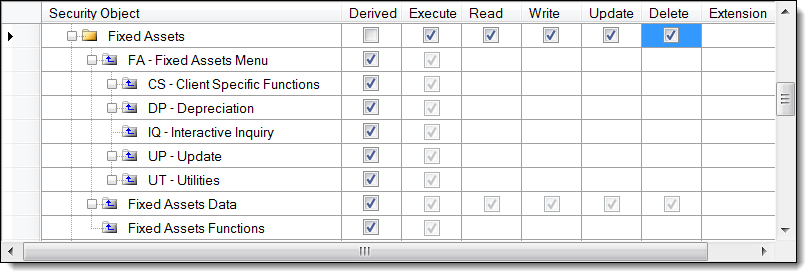
Security Roles are made up of specific security granted to the different security objects within the structure. By default, all the objects are marked as "Derived." Derived security objects inherit the security of the first parent object that is not derived. If none are found, no access to that security node is granted with a particular role.
Creating a New Role
To create a new security role, use the Add ( + ) button in the top toolbar. Enter the new Role ID and Role Title for the role. Set the specific security desired for this role in the Security Object Tree. Select Save to create the new security role.
Editing an Existing Role
Security of the objects within an existing role can be changed by locating the object in the Security Object Tree and changing the security settings in the panel to the right of the tree. If any changes to the role are made, but have not been saved yet, the Save button in the toolbar is enabled. Clicking the button will send all pending changes to the 7i server.
Context-Sensitive User Interface
The security settings for a specific role may change depending on the type of security object you are viewing. E.g., when viewing "Fixed Assets Menu," you may only see one checkbox for "Execute," as opposed to Fixed Assets Data that has checkboxes for Read, Write, Update, Delete, and Execute.
Common Security Settings
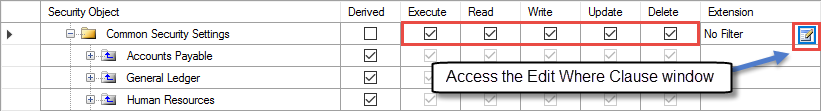
Common security settings allow Where Clauses to be written for tables within roles. Access can be further restricted to tables and linked tables based on a combination of common settings found in all roles assigned to the user.
Where Clause
For folders that are not derived (i.e., Derived box is unchecked), the user can set up Where Clause filters to restrict user security. The Edit Where Clause page displays tabs for each box that is checked on the Manager Security Roles page.
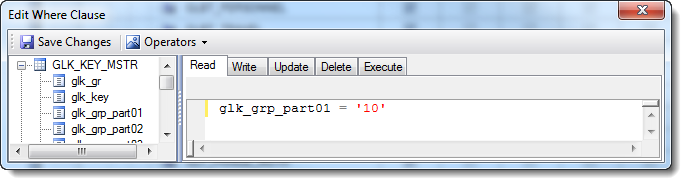
In the example below, a Where clause is written for the Read attribute of the associated table, the GLK_KEY_MSTR. It is possible to include Where clauses for each of the attributes of the table: read, write, update, delete, and execute. In this setup, not only are the tables listed available for restriction based on the Where clause, but the linked tables are restricted as well.
Ledger Security | (glg_gen_mstr) |
| glg_gen_mstr |
| glk_key_mstr |
| glo_obj_mstr |
| glba_budact_mstr |
| bd_eqpt |
| bd_misc |
Account Key Security | (glk_key_mstr) |
| glk_key_mstr |
| glba_budact_mstr |
| bd_eqpt |
| bd_misc |
Object Code Security | (glo_obj_mstr) |
| glo_obj_mstr |
| glba_budact_mstr |
| bd_eqpt |
| bd_misc |
Budget Version Security | (glg_budg_dtl) |
| glba_budact_mstr |
An SQL Where Clause can be entered to restrict access to specific portions of the BusinessPlus data. Each common security item corresponds to a database table, so any column within that table may be used to control security.
The following are some examples of security that can be granted using the General Ledger common items.
Grant access to… | Common item | Where clause |
|---|---|---|
Ledgers "GL" and "PR" | Ledger Security | gl_gr in ('GL','PR') |
All ledgers except "XX" | Ledger Security | gl_gr <> 'XX' |
Fund 10 (assuming FUND is part 1) | Key Security | glk_grp_part01='10' |
Objects 1000-1999 and object 3000 | Object Security | (glo_obj between '1000' and '1999') or glo_obj='3000' |
Budget version "PR" in any ledger | Budget Version Security | gl_bud_cd='PR' |
Budget versions "PR" and "WB" in ledger "GL" | Budget Version Security | gl_gr='GL' and gl_bud_cd in ('PR','WB') |
The above concepts may be combined to produce security that is more complex. Each user may be assigned multiple roles, so it is generally preferable to create simple roles with discrete units of functionality and combine as needed by assigning all relevant roles to the users. The Edit Where Clause screen is not an SQL editor. SQL statements should be entered using the available table columns in combination with the Operators drop-down menu. The screen does not allow SQL comments (i.e., --, /*, */).
In addition to the common security settings, it is necessary to grant access to each table that will be directly accessed by the user. Alternatively, access may be granted at the subsystem level, allowing access to every table within the subsystem. Any additional restrictions defined at the common level will also be applied, regardless of whether access was granted at the table level, the subsystem level, or even the global BusinessPlus level.
Copy Security Role Information
An optimum Security Role design should involve the least possible role overlap. Making good use of layered access and use of discrete reusable security should allow a single role to be reused by many different types of users of the software.
There is a feature that will allow you to copy and paste role information from an existing role into a new role or even replace the role setup of an existing role.
To copy a Security Role, browse to the role you wish to copy and select the "Copy Role" menu item from the Options menu. To create a new role, select the "Add" button from the toolbar and then choose the "Paste Role" menu option from the Options menu. You will need to alter the Role ID to have a unique name in order to save the role.
To replace the security setup of an existing role you would simply browse to the Security Role you wish to replace and select "Paste Role" from the Options menu.
Pasting the role information onto an existing role will replace that role's setup with the new role security. This should be used sparingly and may have undesirable consequences. Once you have saved a replaced role, there is no restore option for the role and its prior setup will be lost. In addition, a rebuild of that role following this change is required.
Tools for Role Definition
Select the Tools menu to select from the following tools:
Rebuild Current Role Security: Rebuilds security for current role only.
Rebuild All Changed Roles and Users: Rebuilds security for all changed roles and users.
Rebuild All Roles and Users: Rebuilds security for all users in all roles without running out of memory.
Jobs
Any jobs that were launched from Manage Security Roles after you opened the plugin can be tracked on the Jobs panel. Select the Jobs menu. Double-click the job number to display available job information.
Tailsheets Security
Admin Console → Manage Security Role → Application Root → Nucleus → Nucleus Functions
A new set of nodes has been introduced within the Manage Security Structure, these nodes provide enhanced functionalities related to security management. Accessible through the Nucleus folder under Nucleus Function, these nodes offer users the ability to view and manage specific aspects of security configurations.
New Nodes:
View Rebuild Security Structure Tailsheet:
Description: This node allows users to view the Tailsheet associated with the job executed when rebuilding the security structure.
Access: Users with Execute Access to this node can access and view the Tailsheet information related to the job.
View Role Import Export Tailsheet:
Description: Users can view the Tailsheet corresponding to the job triggered when performing Role Import or Export operations.
Access: Users need to Execute Access to this node to be able to view the Tailsheet for the respective job.
View User Security Rebuild Tailsheet:
Description: This node enables users to access the Tailsheet linked with the job executed during the rebuilding of user or role security configurations.
Access: Users possessing Execute Access to this node can view the Tailsheet information for the relevant job.
