Multiple Security Objects
Role-based security provides a flexible method of setting up a user's security. What it does not do is provide a quick way of granting access to a particular function of the software. Access to a particular page may provide access to the page, but by itself will not provide access to the data. Additionally, access to the specific tables does not grant access to the Common Security those tables are linked to. The examples below show how access to a specific item in the software requires some level of access to multiple security objects in the structure.
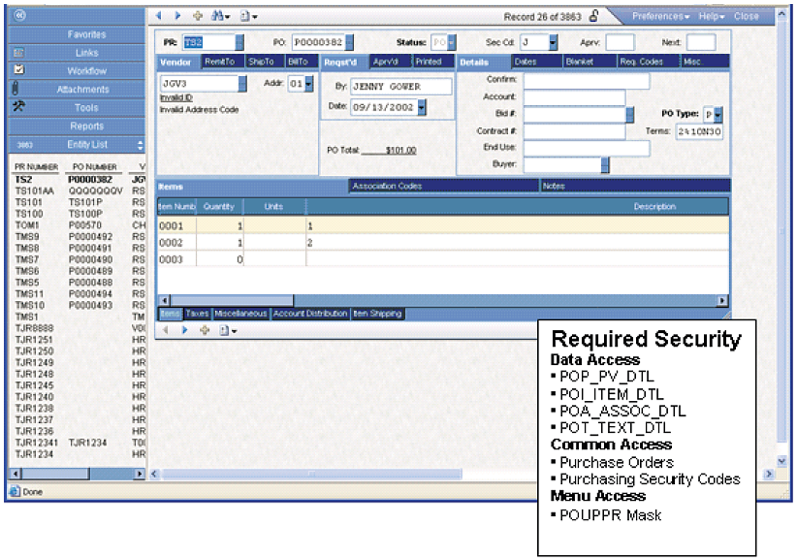
CDD Budget Report
A CDD Budget to Actual report is one of the more common reports. Providing access to this report requires multiple security objects to be granted to the user. To allow a user to run this type of CDD report, access must be granted to:
The tables on the report.
All the common security items the tables are linked to.
The ability to execute a CDD Report.
Access to the CDD Report folder the report resides in.
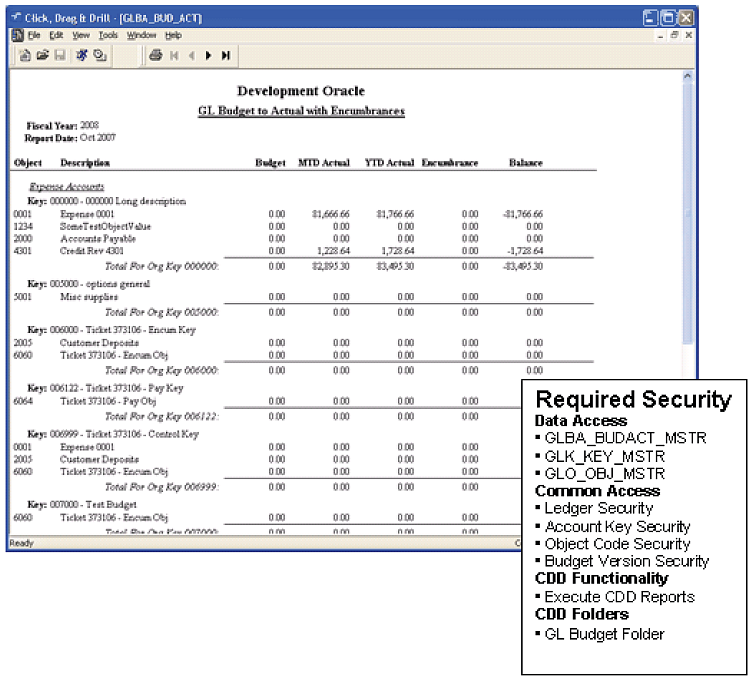
Purchasing Data Entry Page (POUPPR)
Providing access to the mask of a data entry page will allow the page to open but it will not provide access to the data itself. Even providing access to the tables the page references will not necessarily provide access to the Common Security objects those tables reference. And in the case of the Purchasing Data Entry page the list of available Security Codes on the page is also controlled by the Purchasing Security Codes common object.